Visual Gallery
Explore cybersecurity architectures, infrastructure diagrams, and system operations visualizations
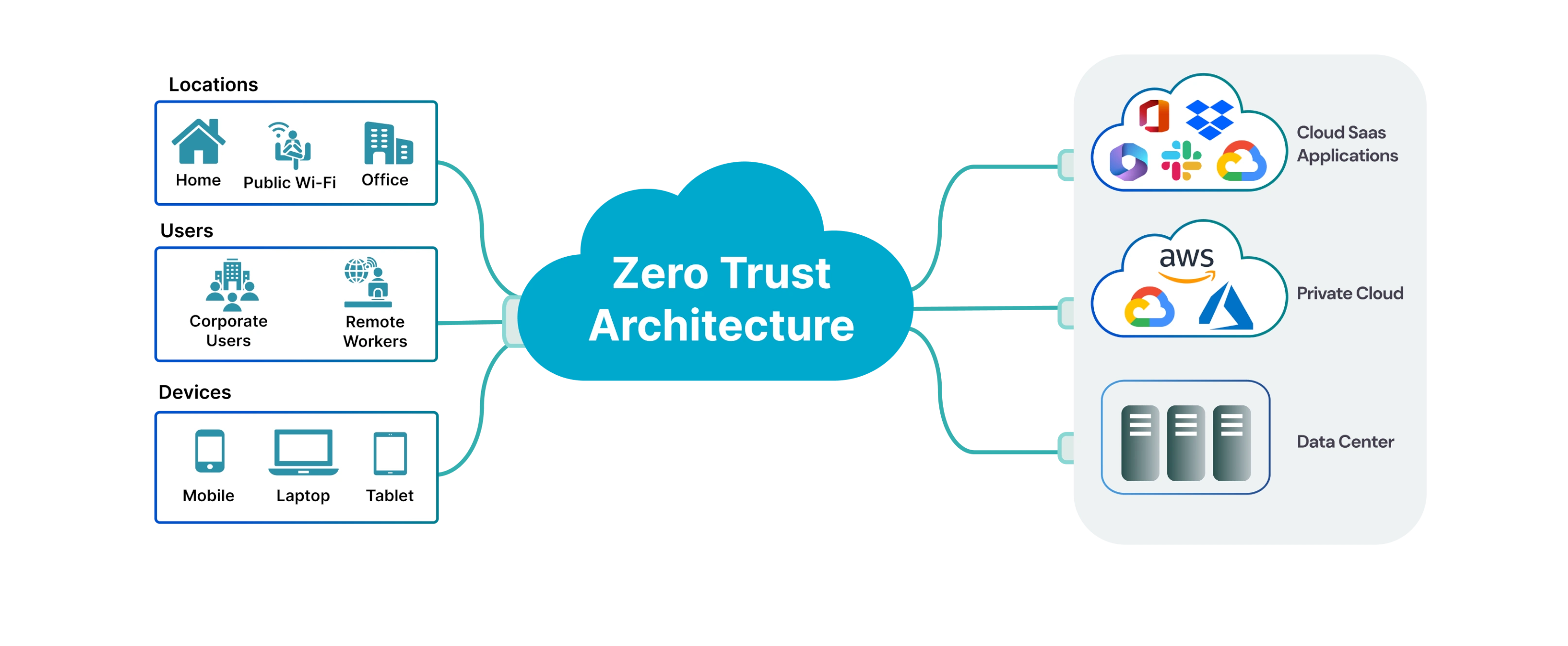
Zero Trust Architecture
Modern security model assuming no implicit trust
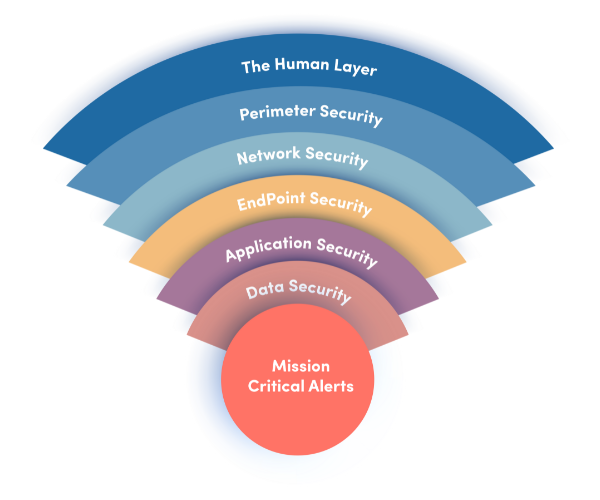
Network Security Layers
Defense-in-depth approach with multiple security layers
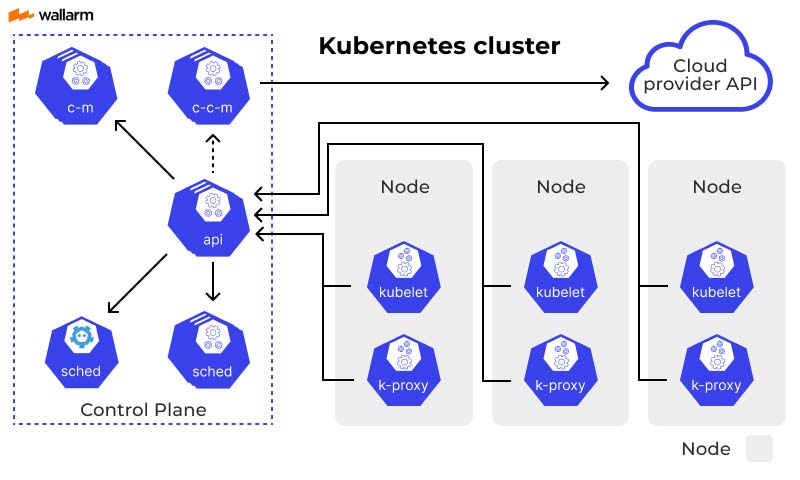
Kubernetes Cluster
Container orchestration platform architecture
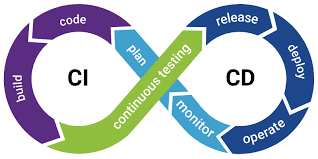
CI/CD Pipeline
Automated software delivery workflow
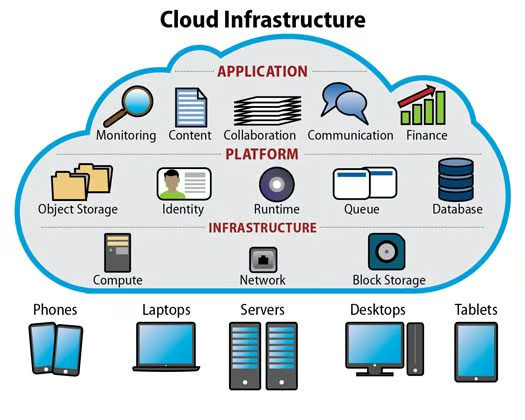
Cloud Infrastructure
Multi-cloud deployment architecture
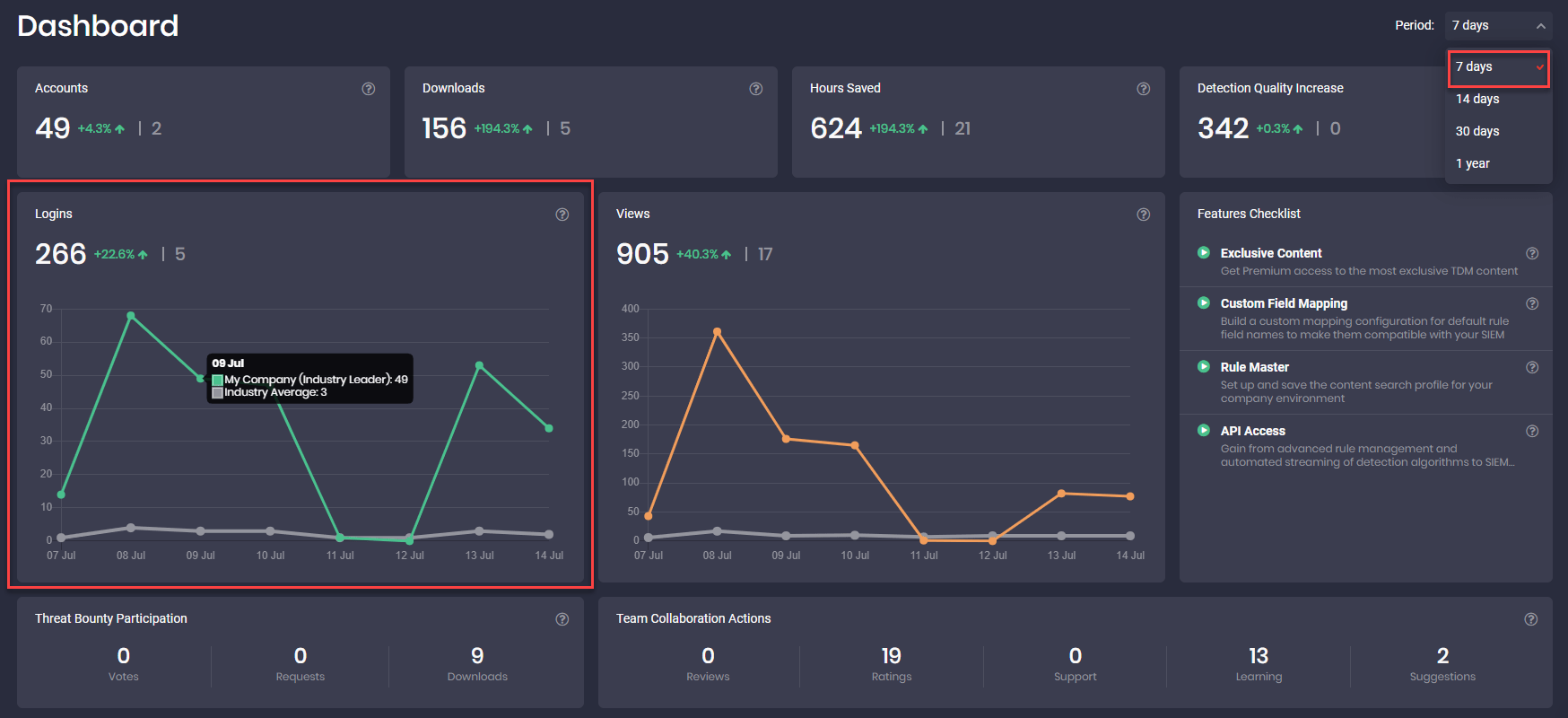
SOC Dashboard
Real-time security monitoring and incident response
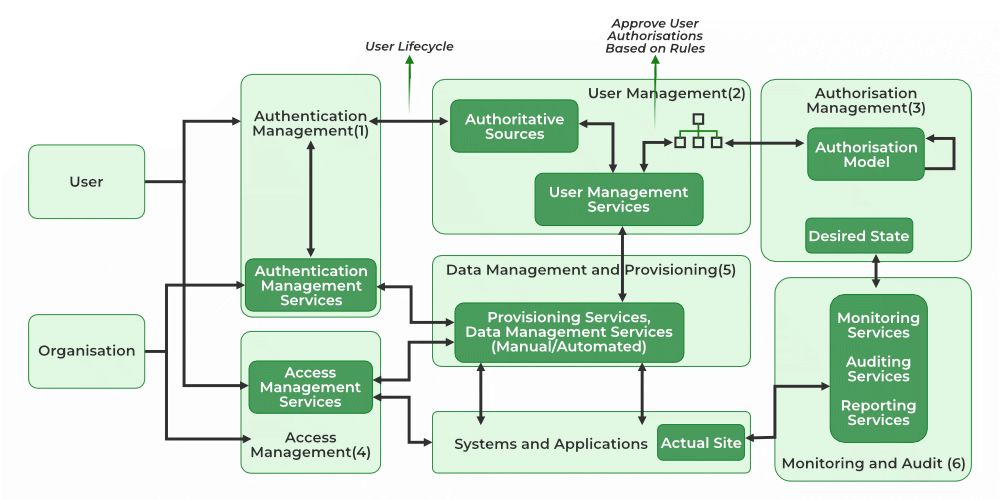
IAM Architecture
Identity and Access Management framework

Penetration Testing
Systematic approach to security testing
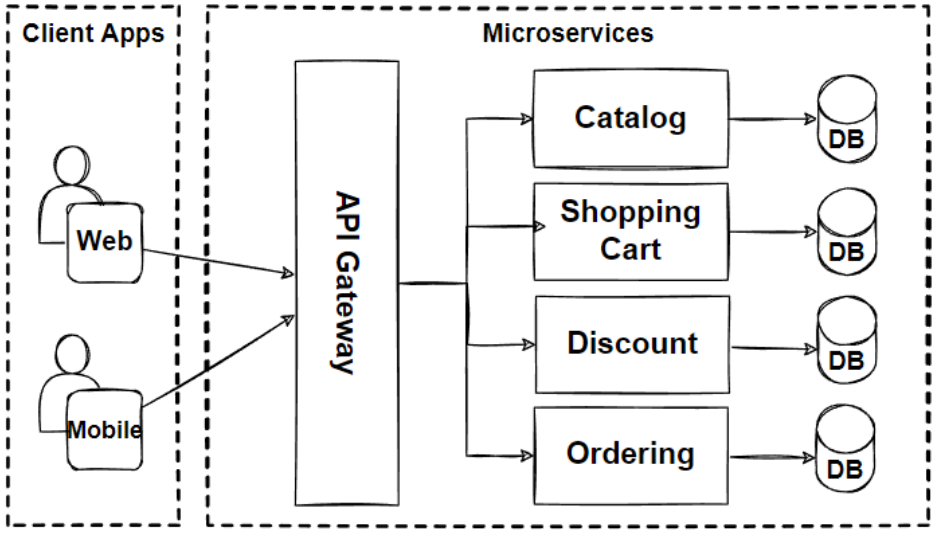
Microservices Architecture
Distributed system design with service mesh
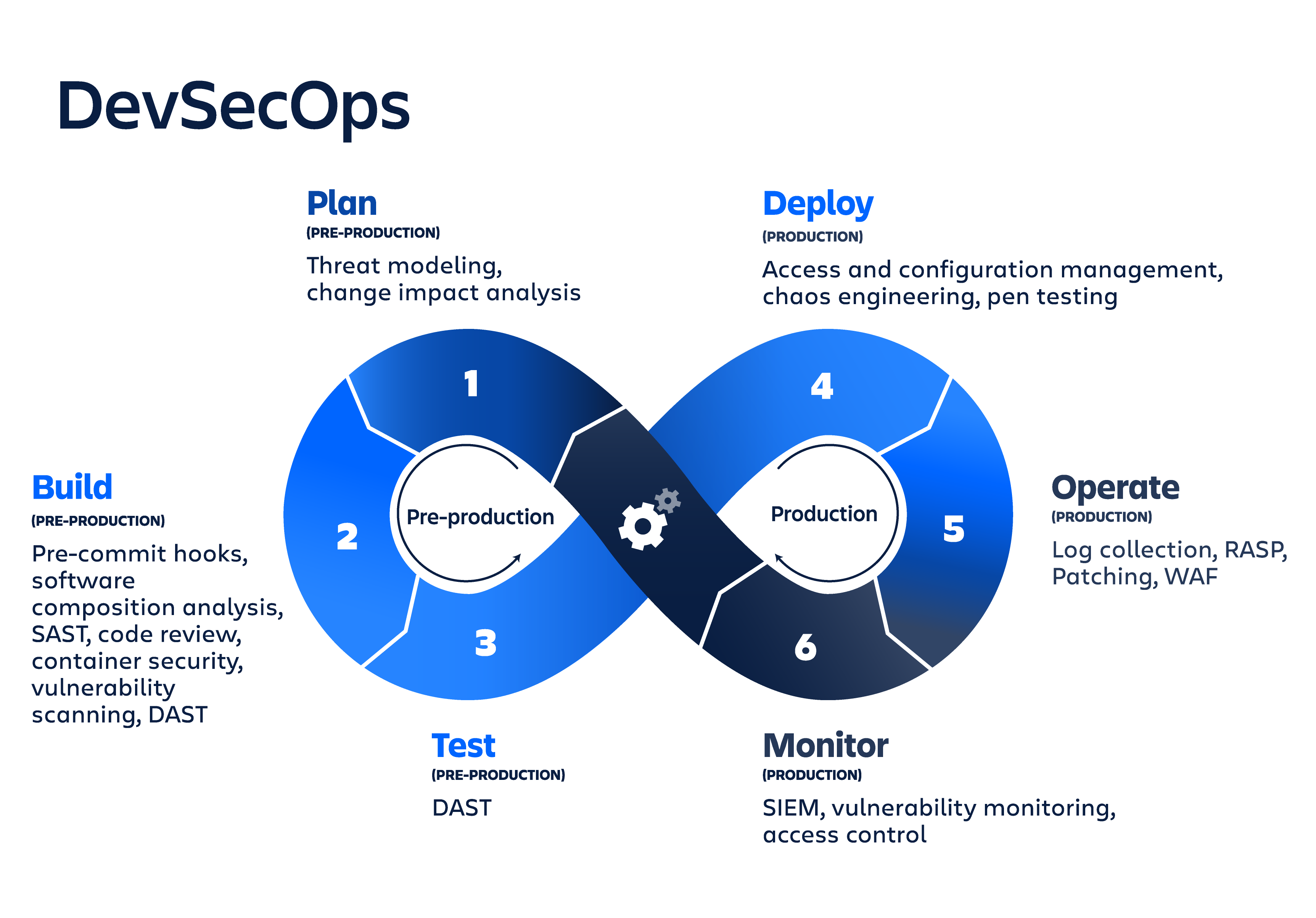
DevSecOps Workflow
Security integrated into development lifecycle
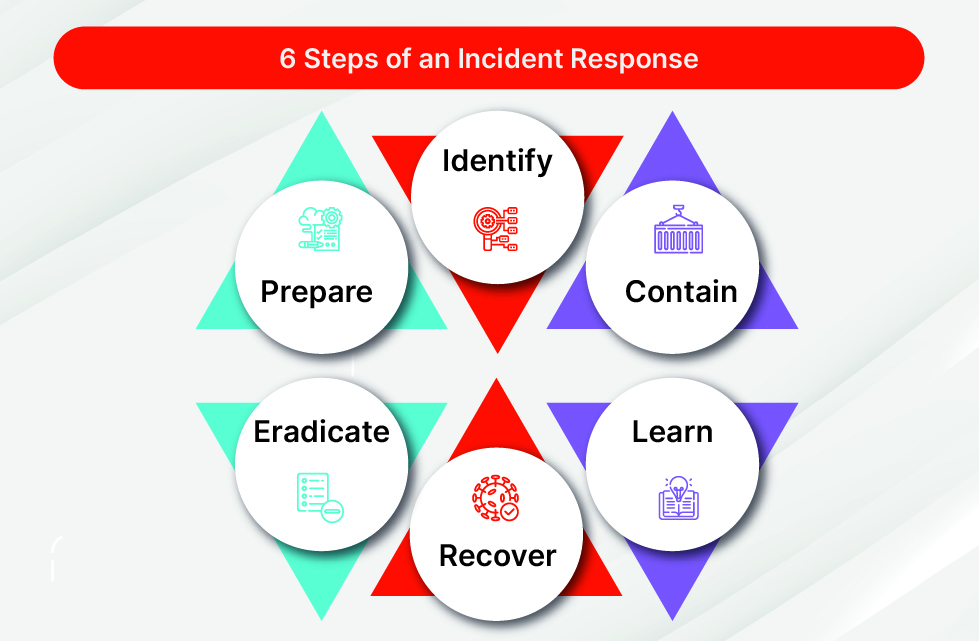
Incident Response
Structured approach to security incidents
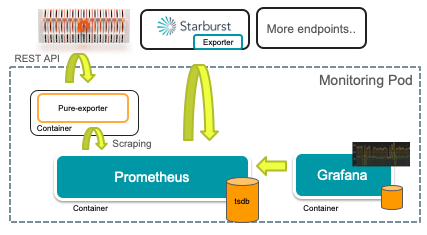
Monitoring Stack
Comprehensive observability platform